Author Archive
Patrick Tucker
Science & Technology Editor
Patrick Tucker is science and technology editor for Defense One. He’s also the author of The Naked Future: What Happens in a World That Anticipates Your Every Move? (Current, 2014). Previously, Tucker was deputy editor for The Futurist for nine years. Tucker has written about emerging technology in Slate, The Sun, MIT Technology Review, Wilson Quarterly, The American Legion Magazine, BBC News Magazine, Utne Reader, and elsewhere.
Patrick Tucker is science and technology editor for Defense One. He’s also the author of The Naked Future: What Happens in a World That Anticipates Your Every Move? (Current, 2014). Previously, Tucker was deputy editor for The Futurist for nine years. Tucker has written about emerging technology in Slate, The Sun, MIT Technology Review, Wilson Quarterly, The American Legion Magazine, BBC News Magazine, Utne Reader, and elsewhere.
Exclusive
Management
ODNI expected to shrink counterintelligence, counterterror centers
The steps are the latest in a series of moves that several current and former officials see as enabling broad vulnerability to foreign espionage attempts.
- Patrick Tucker
Tech
How Trump’s DC takeover could supercharge surveillance
The emergency declaration, combined with new tech, will give government broad new abilities to watch and monitor citizens.
- Patrick Tucker
Defense
Hegseth halves staff of Pentagon’s testing-oversight office
The move may reduce the quality of the Office of the Director, Operational Test and Evaluation’s second opinions, but may not affect safety, former officials said.
- Patrick Tucker
Transition
Gabbard and Patel hearings display diverging views of reality, history along partisan lines
Senators focused mostly on the nominees’ past statements, rather than how they may lead in their prospective positions.
- Patrick Tucker
Defense
‘Extraordinarily dangerous’: Intelligence community insiders warn against Trump’s director of national intelligence pick
Former Rep. Tulsi Gabbard has a “history of irresponsibly promoting misinformation,” said one official.
- Patrick Tucker
Defense
White House issues AI guidelines for national-security agencies
The new memo requires agencies to monitor, assess, and mitigate AI risks related to invasions of privacy, bias, and other human rights abuses.
- Patrick Tucker
Defense
Air Force braces for new nuclear-war scenarios
With more nuclear players and weapons around the world, U.S. forces need to be ready, a top service leader says.
- Patrick Tucker
Tech
Could an easy radio fix have prevented the Trump assassination attempt?
“Being able to talk to other agencies real-time certainly would assist in that response,” one official said.
- Patrick Tucker
Management
Pentagon budget request aims to balance congressional limits, foreign needs, and innovation
“This should be the wake-up call that tells us we need to be buying different stuff,” one expert said.
- Patrick Tucker
Defense
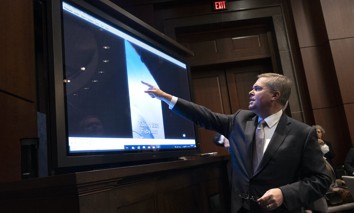
The Pentagon may never get to the bottom of that famous UFO video
The DOD’s office is creating a way for former government employees to reach out with information about UFOs.
- Patrick Tucker
Tech
Agencies get marching orders as White House issues AI-safety directive
The National Institute of Standards and Technology is ordered to draft red-teaming requirements, the National Science Foundation to work on cryptography, and the Homeland Security Department to apply them to critical infrastructure.
- Patrick Tucker
Defense
Lawmakers, Army headed for a fight over cuts to special operations forces
“It doesn’t pass the smell test,” said one Senate staffer.
- Patrick Tucker
Defense
A senator's holds on military nominations are hurting readiness against China, Defense official says
From Defense policy bill amendments and "poison pill" spending bills to promotion holds, Republicans' efforts are frustrating Pentagon officials.
- Patrick Tucker
Defense
Air Force Lab Seeks Higher-Risk, Higher-Reward Breakthroughs
At the Defense One Tech Summit, AFRL's tech chief says the lab wants to answer science questions that have never been asked.
- Patrick Tucker
Defense
US Military Now Has Voice-Controlled Bug Drones
And next year, they might talk back.
- Patrick Tucker
Defense
The Pentagon’s AI Chief Is ‘Scared to Death’ of ChatGPT
But other defense leaders are more eager to deploy new artificial-intelligence tools.
- Patrick Tucker
Defense
Why the Pentagon’s Response to the Discord Leaks Won’t Fix the Problem
The Defense Department keeps too many secrets, uses old approaches to secret storage, and does not apply data-driven strategies to classification.
- Patrick Tucker
Tech
A ‘ChatGPT’ For Satellite Photos Already Exists
Using advanced generative AI and a massive dataset of Earth images, it’s possible to discover objects almost anywhere in just hours.
- Patrick Tucker
Defense
Treasury Sanctions Arms Dealer Who Attempted to Broker Deals Between North Korea and Russia
A new class of “merchants of death” may be emerging from the Russian war on Ukraine
- Patrick Tucker
Defense
Foreign Governments Are Still Targeting Americans on Social Media, NSA Says
U.S. government efforts to stem these infowar efforts are meeting resistance.
- Patrick Tucker