Author Archive
Management
Want to Add 1 Million Jobs to the Economy? Cancel the Sequester Next Fiscal Year
Repealing the cuts could boost near-term output and employment.
- Niraj Chokshi, National Journal
Oversight
The House Is the Most Conservative It's Been in More Than 60 Years
House Republicans are veering right faster than Democrats are pulling left.
- Niraj Chokshi, National Journal
Oversight
That Good-for-Nothing Congress Is Actually Getting More Done
That is, if you measure production by the sheer volume of legislative text it's been passing.
- Niraj Chokshi, National Journal
Pay & Benefits
Defense Workers Take Furloughs in Stride
Bibs for 'Federal Furlough Five-Mile Fun Run' use humor to cope with what amounts to a 20 percent weekly pay cut for 11 weeks.
- Niraj Chokshi, National Journal
Pay & Benefits
Sequestration Concerns Play Out
Budget cuts are eating up 15 percent of some unemployment benefits.
- Niraj Chokshi
Management
Treasury Secretary Lew Cleans Up His Signature for the Nation's Currency
Jacob Lew's signature has gone through an evolution.
- Niraj Chokshi, National Journal
Management
Is a Sequester Tipping Point Coming?
Sequestration was overhyped and the deluge never came. But it may begin to pour this summer.
- Niraj Chokshi, National Journal
Management
Labor Department Offers $2.5 Million in Grants to Improve Bangladeshi Factory Conditions
Applications are due August 2.
- Niraj Chokshi, National Journal
Defense
What Little We Know About the NSA Leaker
Profiles describe Snowden as being fully aware of the risks he took, both in revealing the data and in coming forward.
- Niraj Chokshi, National Journal
Management
Susan Rice Taking Over as National Security Advisor Despite Benghazi Mess
Samantha Power will replace Rice at the U.N.
- Niraj Chokshi, National Journal
Defense
The Banality of Al-Qaida's Scathing Letter to One of Its Operatives
Al Qaida, it turns out, isn't immune from bureaucratic dysfunction.
- Niraj Chokshi, National Journal
Oversight
Analysis: Could Fracking Close the Budget Deficit?
A carbon levy could forestall other more painful choices.
- Niraj Chokshi, National Journal
Oversight
Analysis: The Good Side of the IRS Scandal
Targeting groups was wrong. But the spotlight is now on the important role of the IG.
- Niraj Chokshi, National Journal
Defense
Why the Immigration Plan Really Could Give Us Border Security
Plan requires that a set of border-security goals be met before any undocumented immigrant gets legal status.
- Niraj Chokshi, National Journal
Management
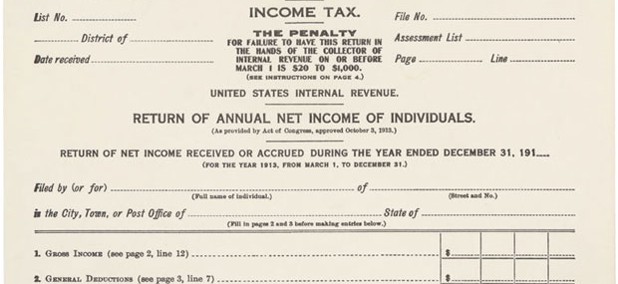
The Income Tax Form Turns 100
The 16th amendment to the Constitution went into effect in 1913.
- Niraj Chokshi, National Journal
Management
Why This Is the Age of Small Government (Sort Of)
By one important measure spending is at a 50-year low.
- Niraj Chokshi, National Journal
Management
Is Chained CPI the Wrong Solution to the Right Problem?
Change might not make benefit adjustments more accurate for everyone.
- Niraj Chokshi, National Journal
Management
There’s Nothing to Fear But the Debt Itself
Federal interest payments are projected to grow faster over the next decade than any other broad category of expenditures.
- Niraj Chokshi, National Journal
Oversight
Nondefense Slice of Domestic Spending on Track to Hit 50-Year Low
Government operations and welfare programs take big hits in both Democratic and GOP plans.
- Niraj Chokshi, National Journal
Management
In the Budget Debate, Even the Definition of Spending Is Up for Grabs
The parties are not able to find a compromise on how to have the conversation.
- Niraj Chokshi, National Journal