Author Archive
Joseph Marks
Contributor
Joseph Marks is a freelance journalist who covered cybersecurity for Nextgov. He previously worked as a staff writer for the Washington Post, covered cybersecurity for Politico, intellectual property for Bloomberg BNA and federal litigation for Law360. He holds a bachelor’s degree in English from the University of Wisconsin in Madison and a master’s in international affairs from Georgetown University.
Joseph Marks is a freelance journalist who covered cybersecurity for Nextgov. He previously worked as a staff writer for the Washington Post, covered cybersecurity for Politico, intellectual property for Bloomberg BNA and federal litigation for Law360. He holds a bachelor’s degree in English from the University of Wisconsin in Madison and a master’s in international affairs from Georgetown University.
Workforce
Government layoffs are making us less safe in cyberspace, experts fear
There’s been a mass exodus of government cyber expertise during the Trump administration.
- Joseph Marks
Pay & Benefits
Judge Tosses OPM Breach Lawsuits, Plaintiffs Appeal
Breached employees can’t show they were actually damaged, the federal judge said.
- Joseph Marks
Advice And Comment
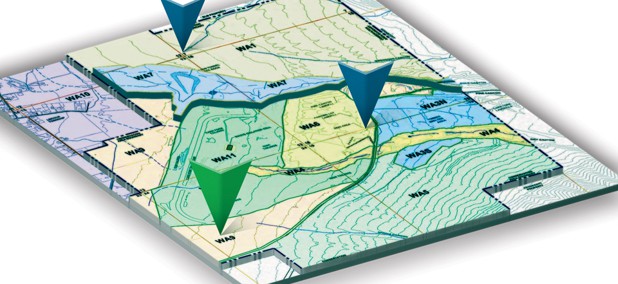
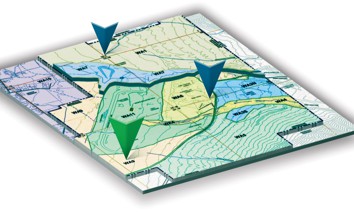
Mapping Better Decisions At EPA
Customizing geographic data helps the agency target pollution problems.
- Joseph Marks
Features
All For One
In a data-driven world, agencies can’t afford to go it alone anymore.
- Joseph Marks
Nextgov
Tech Roundup
Apps that teach, the cyber training slide, CMS’ testing troubles.
- Joseph Marks, Aliya Sternstein and Bob Brewin
Features
New Directions
Lawmakers want to plot a different course for federal chief information officers. That won’t be easy.
- Joseph Marks
Nextgov
Tech Roundup
Ghost viruses, ID iris scans, lagging IT reform.
- Aliya Sternstein, Bob Brewin and Joseph Marks
Briefing
Around Government
Decoding rap and regs, playing to strengths, salary gaps and the sexes.
- Kellie Lunney, Joseph Marks and Eric Katz
Nextgov
Tech Roundup
Amazon’s advantage, a social State Department, paperless VA.
- Bob Brewin, Joseph Marks and Kedar Pavgi
Features
Governing Gets Social
Agencies used to broadcast their messages through social media; now citizens are talking back.
- Joseph Marks
Nextgov
Tech Roundup
Boosting access to federal data, securing mobile devices, the joint health record mess.
- Aliya Sternstein, Bob Brewin and Joseph Marks
Nextgov
Tech Roundup
Transparency moves, TRICARE budget shift and CIOs for IT reform.
- Aliya Sternstein, Bob Brewin and Joseph Marks
Nextgov
Tech Roundup
Rebooting IT, replacing a contracting dinosaur and averting scandal.
- Bob Brewin and Joseph Marks
Features
Welcome to the Data Driven World
The government’s big investment in big data is changing what we know and how we know it.
- Joseph Marks
Management
GSA Releases Draft Solicitation for Massive Professional Services Contract Vehicle
Agencies could purchase a range of services through the proposed OASIS system.
- Joseph Marks
Nextgov
Tech Roundup
Radio plan hits static, digital savings and destination Pinterest.
- Aliya Sternstein, Bob Brewin and Joseph Marks
Nextgov
When the People Speak Is Anyone Listening?
Secession petitions point out strengths and weaknesses of We the People website.
- Joseph Marks
Tech
Agencies want better guidance on BYOD
Reimbursement plans, privacy and legal issues are major challenges, report says.
- Joseph Marks