


For schools across the nation, the start of the new school year marks a time of great joy, excitement and anticipation. Excitement, however, could soon give way to debilitating anxiety once administrators uncover a potential data breach.

Before the mid-2000s, higher education wasn't a common target for cybercriminals. Popular targets were often associated with high-performance, high-yield industries such as banking, manufacturing and retail.
In recent years, this has changed. Due to a confluence of factors such as dwindling security funding and legacy architectures, cybercriminals have found it easy to gain access. On these networks, criminals can establish a presence, elevate credentials and then work toward exfiltrating data with the goal of holding it for ransom.
"[Cyber criminals] have come to prey on the schools, and they've had some success in doing it; What happens is the school has to pay out or find alternatives to bring their environment back online. It's put a lot of schools in a tough spot," says Carmen Paglia, senior systems engineer at ComSource, Inc.
“[Cyber criminals] have come to prey on the schools, and they've had some success in doing it; What happens is the school has to pay out or find alternatives to bring their environment back online. It's put a lot of schools in a tough spot.”
Carmen Paglia, Senior Systems Manager, ComSource, Inc.
Take, for example, a suspected data breach that occurred earlier this year in which the data of approximately 800,000 current and former New York City public school students was made accessible. The information included names, emails and a host of other data points such as disability status and the student's race/ethnicity. Although the provider assured school districts that "no data was subject to misuse," the ramifications had this information been held for ransom would've been disastrous.
For example, one instance of ransomware cost the City of San Antonio approximately $547,000. Although no correlation exists between the two events, one can safely assume that a ransomware attack would’ve cost the New York City Department Of Education hundreds of thousands of dollars.
"Ransomware has run amok," remarks Ron Terra, senior account executive at ComSource, Inc. And at the time of writing, Terra’s statement holds true, as the Los Angeles Unified School District currently goes toe-to-toe with cybercriminals.
However, as LAUSD’s battle with Vice Society continues, one thing is apparent: Partnerships helped LAUSD quickly shut down and mitigate the threat before it was able to cause irreparable harm. So, let’s dive into the benefits of partnerships in cybersecurity, and how it can not only help schools save money, but protect student data.
Addressing the Need for Partnerships in Cybersecurity
To address these increasing threats, Congress approved the State and Local Cybersecurity Grant Program, which allocates approximately $1 billion to schools across the country in order to improve their cybersecurity response.
However, with this increase in funding, what should purchasing committees be looking for? How do they know that a solution is a good one? For decades, enterprise storage solutions were a hefty investment for smaller schools, but with new money flowing into the higher ed space, there is an opportunity to implement high-powered, partner-driven solutions like NetApp's ONTAP, that keeps data security top of mind by focusing on adopting a layered security approach.
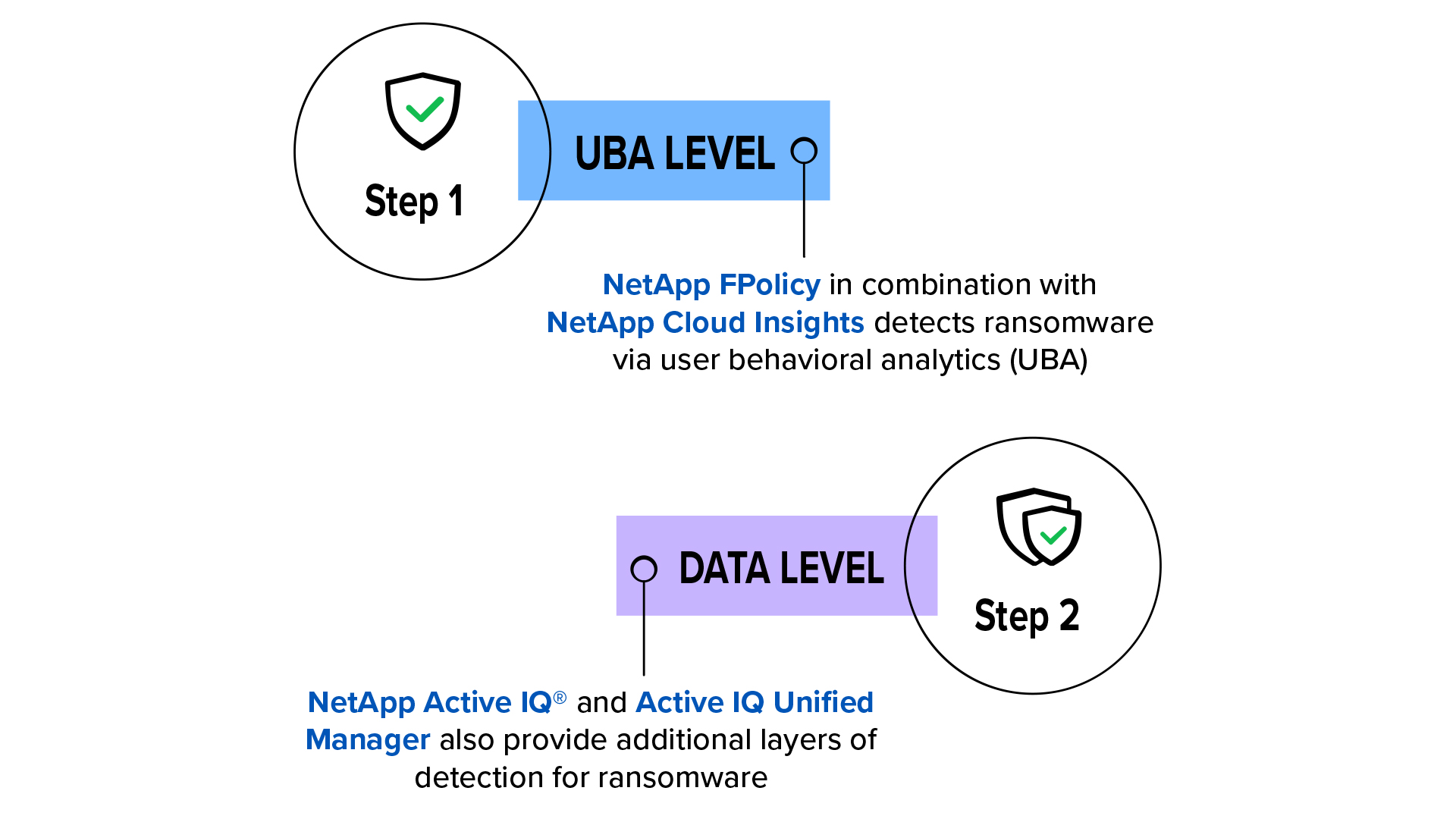
Starting at the user level ONTAP's FPolicy and Cloud Insights solutions monitor users' behaviors on the network. Is a student attempting to elevate their credentials in order to gain root access? Is a teacher trying to access university financial records? FPolicy and Cloud Insights look at these actions and assign risk scores before eventually alerting security analysts to a potential threat actor.
Moving down the security stack, NetApp's Active IQ® and Active IQ Unified Manager analyze your data. For example, a misconfigured app could've given cybercriminals access to your network. And as they prepare to exfiltrate data, Active IQ Unified manager notifies analysts about an uptick in duplicate data.
But the true benefit of NetApp ONTAP goes beyond having tools to combat ransomware. The real advantage of NetApp ONTAP is the dedicated security partners working with you 24/7/365 to ensure round-the-clock protection.
"The problem with cybersecurity is that it's become a noisy part of their industry, and everyone's saying they can help. So how do you weed out the ones that can't and really get to the ones who can," says Terra. "That's where we come in. There are so many factors that go into architecting the right solution, and that's not water you want customers to wade in."
“The problem with cybersecurity is that it's become a noisy part of their industry, and everyone's saying they can help. So how do you weed out the ones that can't and really get to the ones who can.”
Ron Terra, Senior Accountant Executive, ComSource, Inc.
Instead, partnering with experts can help security operations centers build security solutions that are made to address their specific environments, therefore avoiding all of the challenges and frustrations that may come with “going it on your own.”
"You can end up buying a very costly high-performance array when you don't need one, and that affects the bottom line," says Terra. "And that's why value-added resellers like us exist. To help match need with design and implementation because there are a lot of steps, a lot of gotchas and a lot of pitfalls and we can help steer them away from that."
Battling Disparate Data Together: A Brief Data Management Use Case.
Problem: A local school consortium that partners with dozens of local districts in the Syracuse-area initially had disparate data systems. One school district was running VMware, another Microsoft HyperV. For the consortium, managing all of this data was a nightmare.
Solution: Introduce standards across all data platforms via a single vendor solution.
Outcome: ComSource, Inc. crafted a tailor-made solution that featured one source of truth. To ensure engineering staff knew how to operate within the environment, ComSource, Inc. provided on-the-ground training.
Catching Cybercriminals and Quashing Ransomware
As Terra highlighted, a local K-12 consortium consists of an interconnected network of 50 different locations, but the invisible backbone that connects these institutions is its IT system. Schools effectively share threat intelligence, best practices and other information among each other in order to keep student data safe and secure.
By focusing on combating threats together, the K-12 consortium is addressing one of the core recommendations of numerous think tanks: focus on collaboration.
For under-resourced, overburdened districts partnerships can help alleviate the burden that is associated with cybersecurity. Partners are able to delve into the intricacies of each data environment, build solutions based on their observations and then help migrate and train IT departments in this new operating environment.
"When we put these environments in, we know what we're doing. We can move environments over in the middle of the day, and they don't even know it happens," explains Paglia. "I've migrated schools in the middle of the school year from old hardware to their new hardware in the middle of the day while kids are in class."
While migrations like these could take under-resourced schools weeks, for partners like NetApp and Comsource, this is really all in a day’s work.
Looking to Learn More?
Click to learn more about how NetApp ONTAP is helping universities across the nation protect themselves from malicious cybercriminals.